Written by Dimitri Sedashev, Investor
The quest for relevance in Cybersecurity
As digital threats evolve at an unprecedented pace, cybersecurity must continuously adapt. Chief Information Security Officers (CISOs) face the dual challenge of adopting innovative solutions while navigating complex technologies to safeguard their organizations.
According to Crunchbase, funding into cybersecurity businesses bounced back in Q1 of 2024 after several quarters of subdued activity.
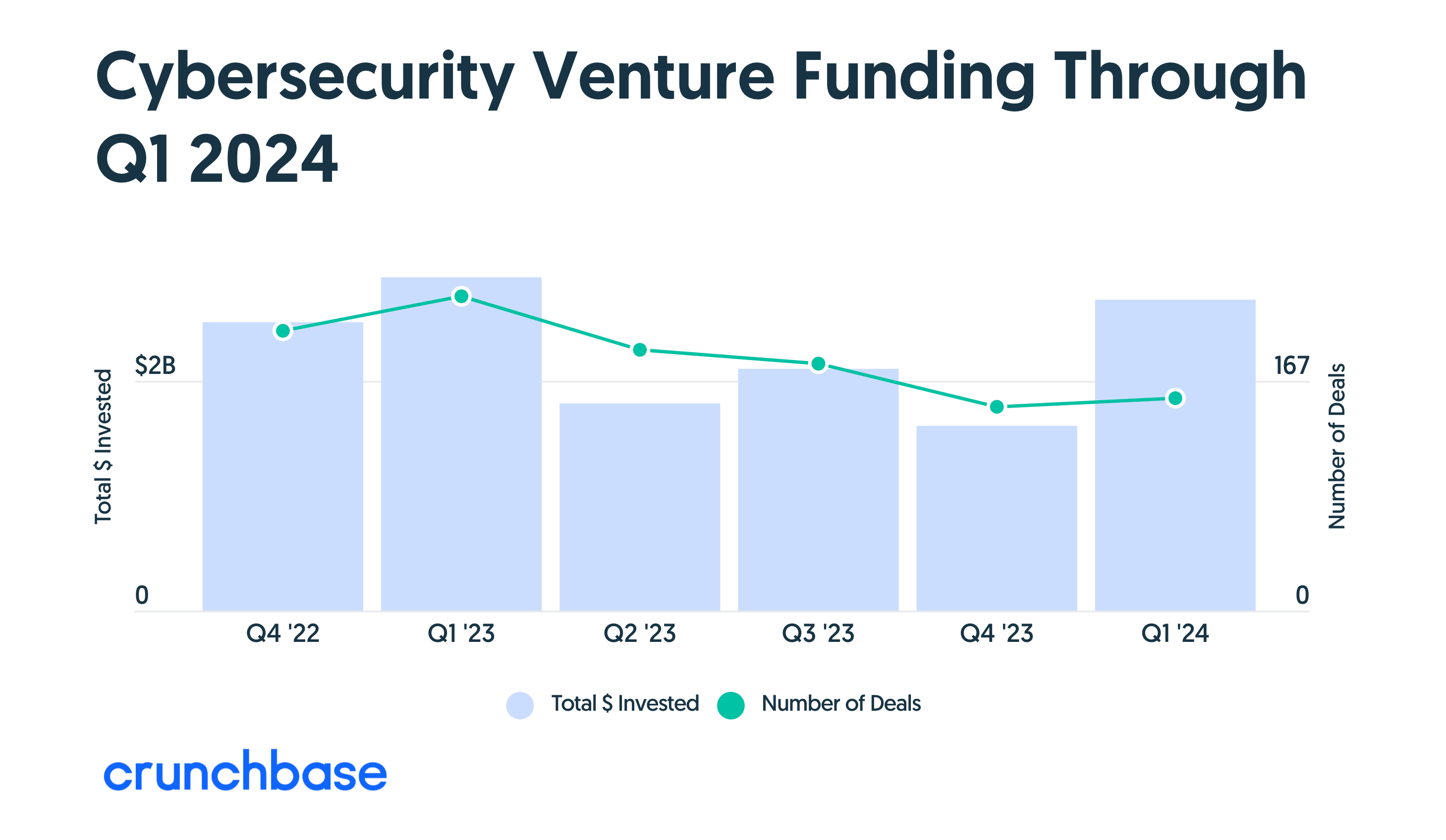
Cybersecurity, like much of B2B SaaS, has been affected by a tough later stage funding environment. However, we also think the sector has been a victim of its own success. 2021 and 2022 attracted so much funding that CISOs were being offered hundreds of tools, whilst in return, their security teams ended up receiving millions of alerts. Over time, along with overworked security teams, it’s become harder to justify the high prices for these security tools, which has led to higher churn of both people and tech. Now, more than ever, we see a focus on ROI, outcomes, and relevance of the product for the company.
The Buying Decisions of the CISO
In enterprise cybersecurity, CISOs grapple with the complexity of managing a stack that, on average, can reach 70+ individual tools. Each addition to this stack demands careful consideration. Tools aren't selected solely for their standalone capabilities, but also for how well they integrate into existing systems. They must contribute to a holistic defense strategy without delivering a poor user experience or hurting productivity.

Streamlining operations and avoiding the addition of more siloed tools to the SaaS sprawl have become key factors in buyer decision-making. The goal is to identify solutions that provide interoperability, strengthen security postures, and deliver actionable intelligence. The challenge is to select solutions that both reinforce and simplify security, advancing a robust, agile, and coherent cybersecurity environment across the organization.
Moving away from long to-do lists
Cloud and application security platforms have greatly enhanced the visibility of security teams across their cloud infrastructures. These tools offer proactive capabilities, detecting vulnerabilities before they can be exploited. Additionally, they have pioneered the contextualization of alerts, simplifying the manual process of prioritizing tasks for security teams. In effect, to show value, ‘more’ was better.
However, years later these platforms are now churning out ever-expanding to-do lists for security teams. This relentless tide of alerts that come from across the stack leads to the all-too-well-known “alert fatigue” and frustration.
The next evolutionary step in cloud and application security will harness cutting-edge innovations and mechanisms to streamline workflows from detection to action. These advancements will enable security professionals to extract crucial insights from vast datasets efficiently. For instance, Aikido integrates cloud vulnerability and application security code scanning tools into a developer-focused platform, empowering developers to be directly involved in remediation
In application security, after several years of trying to shift security left and endless alerts from Software Composition Analysis (SCA) tools, there has been a renewed focus on securing code during production, using deeper and more intelligent contextualisation techniques to help developers. One approach is to examine the runtime context to understand whether vulnerable code is actually being used by the application so that those responsible for remediation can see what’s relevant and what isn’t. Companies like Oligo and Kodem aim to do exactly this by delivering continuous insights into runtime environments. Meanwhile, Escape is delivering immediate time to value in API visibility and security. In the future, we might see application monitoring and Observability techniques further enhancing contextualization, paving the way for automatic remediation at a code level. At a time when the time to exploit is faster than ever, it’s crucial to fix vulnerabilities where they occur.
Improving MTTD and MTTR
Proactive cybersecurity offers greater potential to meaningfully reduce Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). There are early-stage companies approaching this challenge from different angles. Tracebit uses advanced decoy networks in the cloud to quickly identify attackers. On the other hand, Qevlar automates the investigation of alerts as they are triggered from SIEMs, enhancing the accuracy and speed of predicting whether an alert is malicious. Tracecat is developing an open-source security automation platform that builds AI-assisted workflows to orchestrate alerts and resolve cases quickly. This approach streamlines the process by focusing directly on efficient alerts management.
One of the issues with alerts is that they are flagged in isolation across security platforms, making it difficult to grasp the full picture of the risk at hand. Going forward, linking individual alerts across multiple security platforms will provide richer context and clearer risk timelines. With this comprehensive knowledge, teams could respond to risks and threats in hours or minutes, instead of days or weeks.
Transforming Security with Continuous Exposure Management
Attack Surface Management (ASM) remains crucial for helping teams understand their organization’s external security posture. Advances in machine learning now provide more continuous and detailed insights. For example, Hadrian offers customers a unique hacker’s perspective of their organization by simulating continuous attacks to uncover vulnerabilities and providing users with a detailed view of their external attack surface. By contextualizing these vulnerabilities, security teams can identify what is relevant and truly exploitable.
However, ASM alone doesn’t provide a complete view of exposure management. Organizations now use an average of 130 SaaS applications, not including unauthorized ones such as personal email, messaging, and productivity tools used by employees. This proliferation makes it difficult for security teams to track where company data resides and how it is being used. True value comes from tracking identities, classifying data, and understanding the context of actions. Reco offers this now to enterprise customers, and we will likely see more players utilise advanced behavioural AI in SaaS security. With this information, security teams can focus on the real risks posed by malicious behavior or accidents.
Rise of Data in Unified Security Management
Given the challenges associated with managing today’s cybersecurity stack, Unified Security Posture Management (USPM) is becoming the modern orchestration layer. Platforms are emerging to centralize the management and contextualisation of alerts, as well as the remediation of vulnerabilities. We are seeing two main approaches to USPM, one that focuses on the remediation step, and one that focuses on data.
Platforms that focus on managing remediation of vulnerabilities, unify data across multiple security tools, and orchestrate centrally managed workflows to fix them, whether automated or manual. Seemplicity, Dazz, Opus and Zafran are examples of notable contenders here. The space has also generated M&A interest, including Armis’s acquisition of Silk.
We do think there is more opportunity to take a data-centric approach to USPM. Each security tool provides data in the form of alerts and prioritizes these based on a combination of, its own logic and the policies deployed by the customer. The issue is that there is too much data being created by security tools, and customers are missing centralized data stores that inform them accurately of vulnerabilities and their context. Once this data can be structured, then contextualisation of risks becomes more accurate and remediation can be made more efficient. We are excited to see a future where datalakes for cybersecurity are driving decision-making and running automated workflows across organizations.
AI Security: New Tools for Old Problems
AI Security is an emerging segment of cybersecurity, driven by the needs of enterprises and regulated industries to safeguard the adoption of AI technologies. Although its trajectory is still unfolding, we can draw parallels from the evolution of Cloud, SaaS, Big Data, and DevOps.
Previously, critical data and identities were confined within SaaS applications and IT infrastructure. Now, Large Language Models (LLMs) enable these to flow much more freely across organizations, creating entirely new risks that traditional security tools cannot address. In short, businesses need new security tools to tackle these evolving challenges. Knostic is enabling Identity and Access Management for enterprise AI, while Lakera is enabling customers to secure their own GenAI applications against prompt injections and data loss, as well as offering automated GenAI red-teaming. Hidden threats via open-source LLM models will also become a risk for enterprises to navigate as what might appear to be an effective LLM could eventually lead to stolen data by its creators. Mindgard offers multiple layers of AI threat intelligence combined with automated Red Teaming to keep customers prepared for the latest threats.
Embracing the Innovation of Cybersecurity
CISOs and security leaders must navigate the dual challenge of adopting proactive innovations while addressing the complexities these introduce. Europe is poised to play a crucial role in nurturing the next wave of cybersecurity entrepreneurs. Cybersecurity is no longer confined to a single area within IT; now, more than ever, it impacts every part of an organization. Significant overlaps with DevOps, Infrastructure, Cloud, and Data mean that we can expect more entrepreneurs to come from these tech sectors to tackle the cyber threats of tomorrow. By staying ahead of these trends and embracing the complexity of innovation, organizations can build a robust and agile security posture for the future.